“Don’t send your credit card number in an e-mail message!” How many times have you heard that statement? Many times, I hope.
 There is good reason for that statement: normal e-mail messages are sent across the Internet in plain text, and it is easy for many people to intercept these communications. Network sniffers can spy on your email traffic. Using Secure Sockets (SSL) helps, but there is no guarantee that the recipient is taking the same precaution. Even worse, most email servers store all email messages in plain text, messages that can easily be read at any time by email company employees or by any government agency that has an appropriate court order.
There is good reason for that statement: normal e-mail messages are sent across the Internet in plain text, and it is easy for many people to intercept these communications. Network sniffers can spy on your email traffic. Using Secure Sockets (SSL) helps, but there is no guarantee that the recipient is taking the same precaution. Even worse, most email servers store all email messages in plain text, messages that can easily be read at any time by email company employees or by any government agency that has an appropriate court order.
I would never send credit card information or brokerage account information or my Social Security Number or any other sensitive information in an e-mail message. Until now.
In fact, there has been a safe and secure method of sending sensitive information for years: encrypt the information before sending it. Of course, the recipient then receives a message that is unreadable and must decrypt it in some manner before being able to read your message.
NOTE #1: I will point out that many years ago I spent my military service as a crypto technician. For several years, I spent at least eight hours a day maintaining digital electronic devices that encrypted and decrypted digital messages and voice traffic (telephone conversations, aircraft two-way transmissions, etc.). While that was more years ago than I care to admit, I have always maintained an interest in cryptology and have tried to keep up-to-date with the unclassified information available.
I have experimented with all sorts of encryption methods over the years. There are many to choose from, and almost all of them meet their objective of securing communications. However, most traditional methods have been awkward to use and require technical expertise by both parties: both the sender and the recipient needed to know and understand the use of cryptology. Until now.
The Old-Fashioned Method
Perhaps the simplest method, although not the easiest, is to first write the text of the message in a word processor or a text editor, then to encrypt that file with a separate encryption program. There are a number of free encryption and decryption programs available.
NOTE #2: My current favorite fee encryption and decryption program is Encrypto, which I described in an earlier article here. With Encrypto, you can encrypt any file on a Windows computer and send it to someone using Encrypto on a Macintosh or vice versa. Unfortunately, Encrypto is available only for Windows and Macintosh; there is no version available for Android or Apple iOS (iPhone, iPad, or iPod Touch) handheld computers or for Linux. You can find other high-quality encryption products for the other operating systems but most are not compatible with Windows and Macintosh.
Once the message has been written, encrypted, and saved on your computer’s hard drive, you can open your email program and send the encrypted message as an attached file to anyone you wish. However, the recipient also must have the same encryption and decryption program installed on his or her computer in order to decrypt your message. The recipient also needs to know the encryption key you used in order to decrypt the file.
The old-fashioned method of encrypting a message and then sending it by email as an attached file has worked for years and is still a secure solution. However, it is a bit awkward to use, and both the sender and the recipient must be familiar with the various steps needed. Today there is a simpler method of sending secure email messages which I think you will find easier to use as well. The new service is also available FREE of charge.
Tutanota
One new service combines the encryption process with an email program. There is no need to use different programs to write a message, encrypt it, and then send the message by email. Tutanota, a word derived from the Latin words for “secure message,” does all that within one easy-to-use, web-based program. It works sort of like Gmail except that it includes a built-in, high-security encryption and decryption process. When using the program, nobody can read your messages unless they know the encryption key you used. Not even the Tutanota employees can read your messages.
Tutanota’s software is open source. That means the code is freely available to anyone who wishes to look at it to find “back doors” or other security weaknesses. Unlike Gmail, Outlook.com, Yahoo Mail, and most other mail services, hundreds of programmers outside of the company have already examined the source code and have not found any security problems. If new security problems are identified, the fixes are usually applied and implemented quickly, usually within 24 hours. Open source software is generally considered to be much more secure than similar software created by and kept secret by a corporation.
Best of all, Tutanota is a FREE service. It doesn’t even display advertisements. The company does offer a few additional fee-based services, primarily for use in corporate environments where groups of people may need to share encrypted messages. One example might be a stock broker’s employees. However, Tutanota has promised that the present service for individuals will always be available free of charge. After using Tutanota for several months, I haven’t found any reason why I would want to pay for a premium service.
The Tutanota email servers are located in secure data centers in Germany. Since the NSA affair, many people no longer trust service providers from the United States. Having a service provider located in Germany (or another German-speaking country) might not guarantee greater data security or privacy, but the data protection regulations there do give rise to a level of trust more than in many other countries.
All saved data in Tutanota are subject to the German privacy protection laws that are much more strict than the laws of the United States, Canada, or the United Kingdom. Under German laws, a court order from any government demanding private information or messages, even from the German government, is declined. Of course, the German courts already know those laws, so the German government won’t issue any such court orders. Court orders from all other governments are declined, as required by German laws.
Of course, any such court orders would be meaningless anyway. With Tutanota, the information is encrypted in the sender’s computer and remains encrypted throughout the email process until decoded in the recipient’s computer. Even if Tutanota employees were ordered to reveal the information, they simply cannot do so because they can only see the encrypted messages. Any messages intercepted by anyone other than the recipient will look something like this:
ylnjg1h683%nduGGsktDokmV^*j/iO}sW#
Court order or not, an intercepted message is meaningless to anyone who does not know the encryption key. Of course, the same is true for the credit card hacker in Uzbekistan and for your 12-year-old neighbor up the street.
Even Tutanota employees cannot see the encryption key used (there’s no encryption key reset option) so there is no way for those employees or anyone else to be able to decrypt the data they are sending which means they can’t be strong-armed by governments to hand over data. Nor are they data-mining your emails to sell information about your email habits to advertisers the way Gmail and a number of other email providers do.
NOTE #3: There is a major difference between encryption keys and simple passwords. The difference is beyond the scope of this article as (1.) it would be a very long article by itself, and (2.) others have already published such articles explaining the differences. See https://www.linkedin.com/pulse/20140912130912-9768674-encryption-vs-password-protection-a-matter-of-acceptable-risk for one such article explaining the differences between encryption keys and simple passwords.
In short, end-to-end encrypted data cannot be read by the Tutanota employees or by government agencies or by spammers or by any other third party. German law states that email providers cannot be forced to manipulate their software to implement backdoors or other security holes. The Tutanota email service is available free of charge to anyone, including to Americans. There are no U.S. laws (at this time) prohibiting Americans from using secure email services. In fact, if anyone wants to have truly private email conversations, he or she must use an encrypted email service in Germany, Switzerland, Iceland, or a very few other countries that legally require such information be kept private.
Tutanota’s email service can be accessed by using any modern web browser. This means that it operates on Windows, Macintosh, Linux, UNIX, Android, Apple iOS, Blackberry, and other operating systems. In addition, the company has created free apps for Android and Apple iOS systems that simplify the reading and writing of encrypted message on the smaller screens typically used in handheld devices.
Attachments and even the email subject lines are also encrypted as a matter of course by Tutanota. Encryption and decryption of data always happens locally on your device upon login. All data is end-to-end encrypted, and the only people who can access the data are you and the recipient(s) with whom you have shared your encryption key.
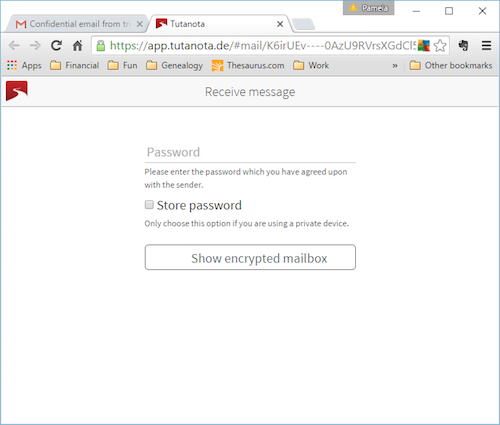
Best of all, the recipient does not need to be a Tutanota user. He or she will receive a short email message in the inbox of their usual email service. That message will advise the recipient that a confidential, encrypted message is available. He or she can then click on a link within the same message. That opens a web browser page with an encrypted SSL link to Tutanota’s email servers. The recipient then must enter the password that you previously agreed upon with them in order to read the message and to write any reply message. The non-Tutanota user cannot create NEW email messages, however. He or she can only securely REPLY to Tutanota messages received. Unlike some other encrypted email services, Tutanota will work well for sending and receiving secure messages to and from anyone who is not a Tutanota user.
However, if the recipient also is a Tutanota user, the sending and receiving of messages is simplified still further. Tutanota automatically encrypts all email sent to another Tutanota address.
You do not need to provide any personal data when signing up with or when using Tutanota. The company says it does not log IP addresses. The IP addresses of sent and received emails are also stripped so that your location remains unknown. The new user can pick his or her own user name in the same manner as Gmail, Yahoo Mail, and other popular web-based email systems. There is no requirement to use a real name or to reveal any address or other personal information. Tutanota’s email services used by most individuals are free, so there is no need to ever supply a credit card number. Should you decide to use one of the company’s paid premium services, it is possible to make a normal payment with a credit card or an anonymous payment with Bitcoins. In short, Tutanota users can remain anonymous, should they wish to do so.
If the user wishes, Tutanota also will send and receive normal plain text (unencrypted) email messages. In other words, you can use Tutanota in place of Gmail, Yahoo Mail, or any other email system for all your email requirements. However, before sending anything that is unencrypted, a pop-up message appears, stating that the message is not secure and requiring the sender to click on an icon to verify that unencrypted email is authorized for this one message.
Secure or not, newsletter editor Pam did find one less than user-friendly shortcoming. When composing a message or attempting to read a received message, the user is prompted for the required password. The word “password” is displayed in a font with colors that do not contrast well against the background. The user has to look hard to find the space for the password. Since I have been using encryption and passwords for most of my life, I expected a place to enter the password and I didn’t see a problem. Pam rarely uses encryption so she didn’t notice the space to fill in the required password until after receiving an error message. She then looked closely and the saw the data entry block for “password.” That’s not a show-stopper but it can cause a bit of confusion.
A Word About Passwords and Encryption Keys
Of course, secrets are only safe if they are properly created. In the case of encryption, the encryption key must be a secret word or phrase that is shared with the recipient. Don’t send the encryption key in another e-mail message! Ideally, it should be agreed upon only in a face-to-face conversation held in an area where no one else is listening.
When telling your recipient about the message you plan to send them, you may find it simpler to refer to your encryption key as a “password.” While there are technical differences, the function is the same: it provides access to your message. Like most passwords, you can mix uppercase and lowercase letters, numbers, and other characters. Also, the longer the word, the better. Don’t use short words like “dog” or “Joe” or “roots.” Use “Rumplestiltskin” or “antidisestablishmentarianism” or “genealogy.” Heck, many people can’t spell that last word anyway! Adding some numbers adds still more security. Even better, combine several words into one or use cryptic acronyms. For instance, the encryption key might be “Iltstwani2016” that stands for “I like to surf the web at night in 2016.” You and your recipient probably can remember that phrase, but the odds of someone else guessing it are slim. Of course, don’t use my example. Create your own!
You could also use “inferred words.” That is, don’t send the recipient the actual words but simply give him or her a hint, such as “Your mother-in-law’s father’s middle name and the name of the cemetery in which he is buried.” You then use the secret words as the “key” for creating the encrypted message. Without that key, your recipient cannot “unlock” the message and read it.
You will want to use different encryption keys (or “passwords”) when exchanging messages with different recipients. Just as you wouldn’t give anyone access to your bank password, each recipient should have a unique key/password to ensure that they can read only the messages intended for them. Also, make sure you can remember the key! There is no reset option or other back door used to recover forgotten encryption keys. If you and your recipient both forget the agreed-upon key, the message(s) will be lost forever.
Summation
The thing that I like most about Tutanota is the ease of use: neither the sender nor the recipient has to have much technical knowledge; almost anyone who can already use Gmail or AOL Mail or other email services can also use Tutanota within a minute or two after creating an account. The sender must have a Tutanota account but the recipient does not. Even non-Tutanota users can securely receive and read encrypted messages and even reply to them securely.
Tutanota works equally well with Windows, Macintosh, Linux, UNIX, Apple iPhone, Android, Blackberry, or most any other operating system. All you need is a standard web browser that supports SSL connections (all modern web browsers will do that). Special apps also are available for Apple and Android mobile devices.
Is it safe? Encryption experts will tell you that no encryption method is perfect. I wouldn’t use Tutanota to send nuclear armament information if I had any.
While I would not entrust our nation’s greatest secrets, Tutanota certainly is much safer than sending sensitive data directly through standard e-mail. The largest threat to Tutanota would be a screen capture virus that images the decrypted message on the recipient’s computer. Such attacks are unlikely, but they are possible in theory.
I am willing to use Tutanota to send my credit card information, my Social Security Number, and even my bank account and credit card information to people I trust.
Most of us probably have more mundane uses for encrypted e-mail messages. For instance, do you want to notify your son-in-law about that “special Christmas present” you are purchasing for your daughter? Do your daughter and son-in-law share the same computer? If so, I’d suggest you use Tutanota to send that messages to “his eyes only.”
The end-to-end encryption, even for users without a Tutanota account, can hardly be surpassed in terms of simplicity, and Tutanota is my preferred solution to offer simple user-friendly encryption. I don’t use Tutanota every day; but, when I need to avoid prying eyes, it has provided a great service.
You can learn more about Tutanota at https://tutanota.com.
Note the “s” in the address: https://tutanota.com. That indicates that “secure sockets” is in use. That is, your web browser is using an encrypted and secure method of communication with tutanota.com, and nobody can intercept any of the information you enter into the web browser.
If you have further questions, you probably will find answers in the extensive FAQs (Frequently-Asked Questions) at http://tutanota.uservoice.com/knowledgebase/topics/69730-english.
Tutanota is also available in 27 different languages. Since you are reading this article in English, I assume that you will want to use the English version as listed in the links in this article. Should you wish to use a different language, go to https://tutanota.com and scroll to the bottom of the page. There you can click on your language of choice.
- China’s new Anti-Terrorism Legislation Requires Surveillance on all Services, including Encrypted Communications
- Microsoft Has Your Encryption Key If You Use Windows 10
Categories: Email Security, Encryption

An optional fee based webmail service is startmail.com, I have been using it for correspondence to financial services I use. It’s easy to use & it’s email servers are in Europe not the USA or Canada.
LikeLike
Wonder if ISIL is aware of Tutanota?
LikeLike
I suspect that ISIL is very aware of Tutanota and of all the other privacy email services plus have probably developed their own encrypted email services as well. I doubt if the presence of any one email service will make much difference to ISIL or any other terrorist operation. These groups seem to be well funded and are very capable of developing their own encryption services, should they wish to do so. The availability of Tutanota or any other encrypted email service is probably of trivial importance to terrorists.
LikeLike